#Telecom Office Attack
Explore tagged Tumblr posts
Text
Mob Vandalizes Telecom Office in Festac Town Amid SIM Blockade
On a scorching afternoon in Festac Town, Lagos, an uproarious scene unfolded at a major telecommunications office. The incident, now widely referred to as the “SIM Blockade,” involved a mob of frustrated locals who took their grievances to the streets, culminating in a significant act of vandalism against the telecom office. The root of this chaos was a recent policy change that left countless…
#Communication Breakdown#Customer Frustration#Festac Town Incident#Mob Vandalism#Nigerian Telecom Issues#Regulatory Response#SIM Blockade#SIM Card Crisis#Telecom Office Attack#Telecom Policy Failure#Touchaheart.com.ng
0 notes
Text
Okay here are some facts I think everyone needs to know about Modi's relationship with the occupation of Kashmir.
-In June/July of 2019, just a few months after Modi took office for his 2nd term he sent ~10,000 soldiers into Kashmir.
-Shirtly after he suspends telecoms/internet and implements a stringent curfew. He also begins arresting political leaders and HRAs. He begins jailing journalist in the dark (no internet made that easy)
-That August he revokes article 370 and 35a which removed Kashmir's special status (which basically means they took awa their statehood and nullified their constitution) and allowed non-Kashmiris to begin purchasing land in the region.
-Under Modi, Kashmir has become the most militarized zone in the world. Not being hyperbolic here. There are some areas of Kashmir where soldiers outnumber civilians.
Basically Modi has spent the last decade turning Kashmir into an open air prison while laying the groundwork for demographic change. Indian tourism in the area has been on a MASSIVE incline. That's why you're seeing messaging from India calling Kashmir "The Switzerland of India" and why tourists were attacked.
If this all sounds familiar that's because Modi is pulling from Netanyahu's playbook. Down to framing his colonization as a security issue. There's a reason he looks up to him.
Modi is a RSS Hindu nationalist that has been heavily inspired by European fascist movements.
You should know all of these facts as you navigate a lot of disinformation that's gonna come at you.
3K notes
·
View notes
Text
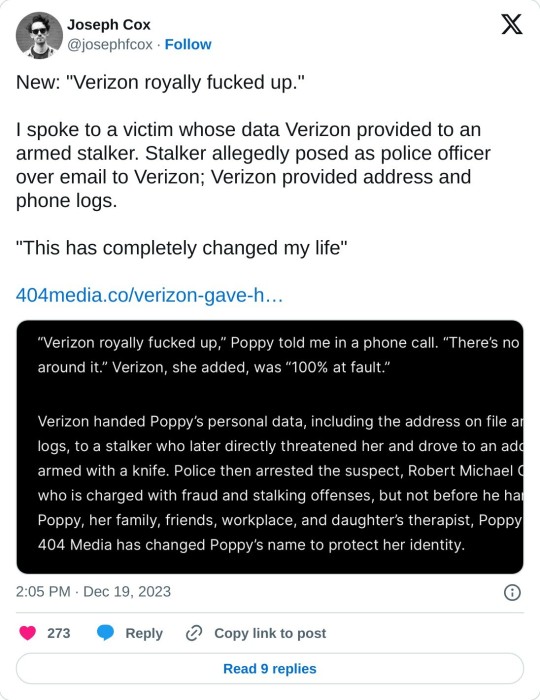
Verizon handed Poppy’s personal data, including the address on file and phone logs, to a stalker who later directly threatened her and drove to an address armed with a knife. Police then arrested the suspect, Robert Michael Glauner, who is charged with fraud and stalking offenses, but not before he harassed Poppy, her family, friends, workplace, and daughter’s therapist, Poppy added. 404 Media has changed Poppy’s name to protect her identity.
Glauner’s alleged scheme was not sophisticated in the slightest: he used a ProtonMail account, not a government email, to make the request, and used the name of a police officer that didn’t actually work for the police department he impersonated, according to court records. Despite those red flags, Verizon still provided the sensitive data to Glauner.
Remarkably, in a text message to Poppy sent during the fallout of the data transfer, a Verizon representative told Poppy that the corporation was a victim too. “Whoever this is also victimized us,” the Verizon representative wrote, according to a copy of the message Poppy shared with 404 Media. “We are taking every step possible to work with the police so they can identify them.”
In the interview with 404 Media, Poppy pointed out that Verizon is a multi-billion dollar company and yet still made this mistake. “They need to get their shit together,” she said.
Poppy’s story highlights the very real human cost of a massive failure on Verizon’s part. More broadly, it highlights the increasing problem of criminals filing fraudulent emergency data requests (EDRs) with tech companies and telecoms as a way to trick them into handing over their targets’ data. Other criminals who discuss the practice are often part of wider criminal groups that rob, shoot, and attack one another and outside victims, according to Telegram messages reviewed by 404 Media. Senators have written to tech companies for information on the problem of fake EDRs, and one company has emerged which attempts to mitigate the problem by vetting requests from police departments. And yet, the issue remains.
“This has completely changed my life, for the rest of my life,” Poppy said, adding that the incident has amplified her PTSD and anxiety from previous trauma.
3K notes
·
View notes
Text
Every year has its own mix of digital security debacles, from the absurd to the sinister, but 2024 was particularly marked by hacking sprees in which cybercriminals and state-backed espionage groups repeatedly exploited the same weakness or type of target to fuel their frenzy. For attackers, the approach is ruthlessly efficient, but for compromised institutions—and the individuals they serve—the malicious rampages had very real consequences for people's privacy, safety, and security.
As political turmoil and social unrest intensify around the world, 2025 will be a complicated—and potentially explosive—year in cyberspace. But first, here's WIRED's look back on this year's worst breaches, leaks, state-sponsored hacking campaigns, ransomware attacks, and digital extortion cases. Stay alert, and stay safe out there.
China's Salt Typhoon Telecom Breaches
Espionage operations are a fact of life, and relentless Chinese campaigns have been a constant in cyberspace for years now. But the China-linked espionage group Salt Typhoon carried out a particularly noteworthy operation this year, infiltrating a slew of US telecoms including Verizon and AT&T (plus others around the world) for months. And US officials told reporters earlier this month that many victim companies are still actively attempting to remove the hackers from their networks.
The attackers surveilled a small group of people—less than 150 by current count—but they include individuals who were already subject to US wiretap orders as well as state department officials and members of both the Trump and Harris presidential campaigns. Additionally, texts and calls from other people who interacted with the Salt Typhoon targets were inherently also caught up in the espionage scheme.
Snowflake Customer Breaches
Throughout the summer, attackers were on a tear, breaching prominent companies and organizations that were all customers of the cloud data storage company Snowflake. The spree barely qualifies as hacking, since cybercriminals were simply using stolen passwords to log in to Snowflake accounts that didn't have two-factor authentication turned on. The end result, though, was an extraordinary amount of data stolen from victims including Ticketmaster, Santander Bank, and Neiman Marcus. Another prominent victim, the telecom giant AT&T, said in July that “nearly all” records relating to its customers' calls and texts from a seven-month stretch in 2022 were stolen in a Snowflake-related intrusion. The security firm Mandiant, which is owned by Google, said in June that the rampage impacted roughly 165 victims.
In July, Snowflake added a feature so account administrators could make two-factor authentication mandatory for all of their users. In November, suspect Alexander “Connor” Moucka was arrested by Canadian law enforcement for allegedly leading the hacking spree. He was indicted by the US Department of Justice for the Snowflake tear and faces extradition to the US. John Erin Binns, who was arrested in Turkey for an indictment related to a 2021 breach of the telecom T-Mobile, was also indicted on charges related to the Snowflake customer breaches.
Change Healthcare Ransomware Attack
At the end of February, the medical billing and insurance processing company Change Healthcare was hit with a ransomware attack that caused disruptions at hospitals, doctor's offices, pharmacies, and other health care facilities around the US. The attack is one of the all-time largest breaches of medical data, impacting more than 100 million people. The company, which is owned by UnitedHealth, is a dominant medical billing processor in the US. It said days after the attack started that it believed ALPHV/BlackCat, a notorious Russian-speaking ransomware gang, was behind the assault.
Personal data stolen in the attack included patient phone numbers, addresses, banking and other financial information, and health records including diagnoses, prescriptions, and treatment details. The company paid a $22 million ransom to ALPHV/BlackCat at the beginning of March in an attempt to contain the situation. The payment seemingly emboldened attackers to hit health care targets at an even greater rate than usual. With ongoing, rolling notifications to more than 100 million victims—with more still being discovered—lawsuits and other blowback has been mounting. This month, for example, the state of Nebraska sued Change Healthcare, alleging that “failures to implement basic security protections” made the attack much worse than it should have been.
Russia's Midnight Blizzard Hit Microsoft
Microsoft said in January that it had been breached by Russia's “Midnight Blizzard” hackers in an incident that compromised company executives' email accounts. The group is tied to the Kremlin's SVR foreign intelligence agency and is specifically linked to SVR's APT 29, also known as Cozy Bear. After an initial intrusion in November 2023, the attackers targeted and compromised historic Microsoft system test accounts that then allowed them to access what the company said were “a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions.” From there, the group exfiltrated “some emails and attached documents.” Microsoft said that the attackers seemed to be looking for information about what the company knew about them—in other words, Midnight Blizzard doing reconnaissance on Microsoft's research into the group. Hewlett-Packard Enterprise (HPE) also said in January that it had suffered a corporate email breach attributed to Midnight Blizzard.
National Public Data
The background check company National Public Data suffered a breach in December 2023, and data from the incident started showing up for sale on cybercriminal forums in April 2024. Different configurations of the data cropped up again and again over the summer, culminating in public confirmation of the breach by the company in August. The stolen data included names, Social Security numbers, phone numbers, addresses, and dates of birth. Since National Public Data didn't confirm the breach until August, speculation about the situation grew for months and included theories that the data included tens or even hundreds of millions of Social Security numbers. Though the breach was significant, the true number of impacted individuals seems to be, mercifully, much lower. The company reported in a filing to officials in Maine that the breach affected 1.3 million people. In October, National Public Data's parent company, Jerico Pictures, filed for Chapter 11 bankruptcy reorganization in the Southern District of Florida, citing state and federal investigations into the breach as well as a number of lawsuits that the company is facing over the incident.
Honorable Mention: North Korean Cryptocurrency Theft
A lot of people steal a lot of cryptocurrency every year, including North Korean cybercriminals who have a mandate to help fund the hermit kingdom. A report from the cryptocurrency tracing firm Chainalysis released this month, though, underscores just how aggressive Pyongyang-backed hackers have become. The researchers found that in 2023, hackers affiliated with North Korea stole more than $660 million across 20 attacks. This year, they stole roughly $1.34 billion across 47 incidents. The 2024 figures represent 20 percent of total incidents Chainalysis tracked for the year and a whopping 61 percent of the total funds stolen by all actors.
The sheer domination is impressive, but the researchers emphasize the seriousness of the crimes. “US and international officials have assessed that Pyongyang uses the crypto it steals to finance its weapons of mass destruction and ballistic missiles programs, endangering international security,” Chainalysis wrote.
10 notes
·
View notes
Text
Dec. 28 (UPI) -- Chinese hackers called Salt Typhoon have infiltrated a ninth telecommunications firm, gaining access to information about millions of people, U.S. cybersecurity officials say.
The FBI is investigating the Salt Typhoon attacks, which are spurring new defensive measures, deputy U.S. national security adviser Anne Neuberger told reporters on Friday.
"As we look at China's compromise of now nine telecom companies, the first step is creating a defensible infrastructure," she said.
The hackers primarily are targeting individuals and organizations involved in political or governmental activities and a significant number of hacking victims are located in the Washington D.C.-Virginia area.
The hackers can geolocate millions of people in the United States, listen to their phone conversations and record them whenever they like, Politico reported.
Among recent victims are President-elect Donald Trump, Vice President-elect JD Vance and several Biden administration officials.
Neuberger did not name the nine telecommunications firms that have been hacked, but said telecommunications firms and others must do more to improve cybersecurity and protect individual customers.
"We wouldn't leave our homes, our offices unlocked," she said. "Yet, the private companies owning and operating our critical infrastructure often do not have the basic cybersecurity practices in place that would make our infrastructure riskier, costlier and harder for countries and criminals to attack."
She said companies need better management of configuration, better vulnerability management of networks and better work across the telecom sector to share information when incidents occur.
"However, we know that voluntary cybersecurity practices are inadequate to protect against China, Russia and Iran hacking our critical infrastructure," Neuberger said.
Australian and British officials already have enacted telecom regulations "because they recognize that the nation's secrets, the nation's economy relies on their telecommunications sector."
Neuberger said her British counterparts told her they would have detected and contained Salt Typhoon attacks faster and minimized their spread and impact.
"One of the most concerning and really troubling things we deal with is hacking of hospitals [and] hacking of healthcare data," Neuberger said. "We see Americans' sensitive healthcare data, sensitive mental health procedures [and] sensitive procedures being leaked on the dark web with the opportunity to blackmail individuals with that."
She said federal regulators are updating existing rules and implementing new ones to counteract the cyberattacks and threats from Salt Typhoon and others.
The Department of Justice on Friday issued a rule prohibiting or restricting certain types of data transactions with certain nations or individuals who might have an interest in that data.
The protected information includes those involving government-related data and bulk sensitive personal data of individuals that could pose an unacceptable risk to the nation's national security.
The Department of Health and Human Services likewise issued a proposed rule to improve cybersecurity and protect the nation's healthcare system against an increasing number of cyberattacks.
The proposed HHS rule would require health insurers, most healthcare providers and their business partners to improve cybersecurity protections for individuals' information that is protected by the Health Insurance Portability and Accountability Act of 1996.
"The increasing frequency and sophistication of cyberattacks in the healthcare sector pose a direct and significant threat to patient safety," HHS Deputy Secretary Andrea Palm said Friday.
"These attacks endanger patients by exposing vulnerabilities in our healthcare system, degrading patient trust, disrupting patient care, diverting patients and delaying medical procedures."
The proposed rule "is a vital step to ensuring that healthcare providers, patients and communities are not only better prepared to face a cyberattack but are also more secure and resilient," Palm added.
Neuberger estimated the cost to implement improved cybersecurity to thwart attacks by Salt Typhoon and others at $9 billion during the first year and $6 billion for years 2 through 5.
"The cost of not acting is not only high, it also endangers critical infrastructure and patient safety," she said, "and it carries other harmful consequences."
The average cost of a breach in healthcare was $10.1 million in 2023, but the cost is nearing $800 million from a breach of Change Healthcare last year.
Those costs include the costs of recovery and operations and, "frankly, in the cost to Americans' healthcare data and the operations of hospitals affected by it," Neuberger said.
The Federal Communications Commission also has scheduled a Jan. 15 vote on additional proposed rules to combat Salt Typhoon and other hackers.
6 notes
·
View notes
Text

5 Things to Know for July 19: GOP Convention, Cyber Outages, Ukraine Aid, Olympics Security, Climate Protests
1. Republican Convention
Former President Donald Trump accepted his third GOP nomination for president at the Republican National Convention on Thursday night. In his first public address since an assassination attempt at a Pennsylvania rally last week, Trump called for unity and reiterated key campaign promises on the economy and border security, while also repeating false election claims. Meanwhile, President Joe Biden, isolating in Delaware due to Covid-19, faces increasing pressure from Democratic Party leaders to abandon his re-election campaign.
2. Cyber Outages
A global computer outage has grounded flights around the world, affecting major US carriers such as Delta, United, and American Airlines, resulting in widespread delays and cancellations. The issue stems from a software update by cybersecurity firm CrowdStrike, which assured that it was “not a security incident or cyberattack” and that a fix has been deployed. Banks and telecom companies in Australia and New Zealand, as well as Israel’s hospitals and health services, have also reported computer malfunctions.
3. Ukraine Aid
Germany plans to halve its military aid to Ukraine next year, amid concerns that US support might diminish if Donald Trump returns to the White House. Germany’s military resources have been strained by decades of underinvestment and recent arms supplies to Kyiv. Germany hopes Ukraine can meet its needs with $50 billion in loans from frozen Russian assets approved by the Group of Seven. Anxiety grows in Europe as Trump’s VP pick, Sen. JD Vance, opposes military aid for Ukraine and signals a potential decrease in US defense support for Europe.
4. Olympics Security
Final preparations are underway for the 2024 Paris Olympics, with heightened security measures in place as the Olympic Village begins to welcome athletes. A police officer was recently attacked in central Paris, raising concerns ahead of the Games. This follows another violent incident involving a soldier earlier in the week. French officials are committed to strengthening security as the Games are expected to attract around 15 million visitors.
5. Climate Protests
Five activists from the Just Stop Oil environmental campaign have been sentenced to prison for blocking a major London highway in 2022. The group demands an international treaty to end the extraction and burning of oil and coal by 2030. Their high-profile protests have included spray painting cultural heritage sites, targeting artworks, and disrupting sporting events. The sentences have drawn criticism from environmental agencies and scientists, with Just Stop Oil calling the decision “an obscene perversion of justice.”
3 notes
·
View notes
Text
Cyber Security Jobs Salary in India: A Lucrative Career Path in the Digital Age

As digital transformation accelerates across industries, cyber threats have grown in both volume and complexity. Today, cybersecurity is no longer just an IT concern—it’s a critical business function. With this surge in demand, cybersecurity has emerged as one of the most rewarding and future-proof career domains in India and globally.
At Jaro Education, we consistently guide professionals toward high-growth tech careers, and cybersecurity is among the top-recommended fields for long-term job security, relevance, and financial growth. In this article, we explore cybersecurity job roles, the average salary for each, and what it takes to succeed in this ever-evolving field.
Why Cybersecurity is a High-Paying Domain
The increase in data breaches, ransomware attacks, and cloud vulnerabilities has made organizations highly dependent on skilled cybersecurity professionals. From banks and hospitals to startups and government institutions, all sectors require robust security frameworks, making cybersecurity experts indispensable.
Cyber Security Job Roles and Average Salaries in India
1. Cyber Security Analyst
Average Salary: ₹5 – ₹8 LPA
Top Earners: ₹12+ LPA Cybersecurity analysts are responsible for monitoring and defending an organization’s networks and systems. They conduct vulnerability testing and respond to security breaches.
Required Skills: Network security, SIEM tools, firewalls, incident response
2. Ethical Hacker / Penetration Tester
Average Salary: ₹6 – ₹10 LPA
Top Earners: ₹20+ LPA Ethical hackers simulate cyberattacks to identify security weaknesses in systems before malicious hackers do.
Required Skills: CEH certification, Kali Linux, Metasploit, scripting
3. Security Architect
Average Salary: ₹20 – ₹30 LPA
Top Earners: ₹40+ LPA Security architects design and implement secure network infrastructures and oversee security protocols at the enterprise level.
Required Skills: Cybersecurity frameworks, network architecture, risk assessment, cryptography
4. Chief Information Security Officer (CISO)
Average Salary: ₹40 – ₹80 LPA
Top Earners: ₹1 Cr+ CISOs lead the security strategy for an entire organization. This executive-level role comes with great responsibility and equally high rewards.
Required Skills: Leadership, risk management, compliance, strategy
5. Security Consultant
Average Salary: ₹10 – ₹20 LPA Security consultants work independently or with firms to evaluate a company’s cybersecurity needs and provide solutions.
Required Skills: Communication, cybersecurity tools, policy development, auditing
6. Incident Responder / SOC Analyst
Average Salary: ₹6 – ₹12 LPA These professionals are the first line of defense when a cyber incident occurs. Their role includes threat detection, containment, and recovery.
Required Skills: SIEM, malware analysis, digital forensics, real-time monitoring
Factors That Influence Cybersecurity Salaries
Experience & Certifications: Professionals with certifications such as CISSP, CEH, CISM, or CompTIA Security+ command higher salaries.
Industry: Sectors like banking, e-commerce, telecom, and healthcare tend to pay more due to the sensitivity of their data.
Location: Cities like Bengaluru, Hyderabad, Mumbai, and Gurgaon offer better compensation packages.
Company Size: MNCs and tech giants typically offer better pay and global exposure.
Career Pathways and Education
To pursue a cybersecurity career, one may start with a B.Tech in IT/CS or BCA, followed by specialized certifications or a Master’s degree in Cybersecurity or Information Security.
Jaro Education, in collaboration with premier institutions, offers industry-relevant cybersecurity programs tailored for working professionals and freshers alike. These programs focus on:
Network and system security
Ethical hacking and penetration testing
Cloud and application security
Compliance and governance
Final Thoughts
With increasing digital adoption, cybersecurity professionals are among the most sought-after and well-compensated experts in the tech industry today. Whether you're an IT fresher, a system administrator, or a software engineer looking to pivot, cybersecurity offers tremendous scope for growth, stability, and high income.
0 notes
Text
Stellar Innovations CEO Anish Thomas on Disrupting Outsourcing with Tech-First Excellence
Stellar Innovations, founded in 2016 in Bangalore, has rapidly grown from a small, self-funded team into a global technology powerhouse with 1,600 employees across three continents. In this exclusive conversation, Stellar Innovations Pvt Ltd CEO Anish Thomas shares insights on the company's incredible journey—from humble beginnings to becoming a leader in tech-enabled outsourcing solutions. Discover how Stellar Innovations leverages deep technology, AI, and trust-driven culture to stay ahead in high-stakes sectors like mortgage tech, cybersecurity, and genomics.
How Did Stellar Innovations Begin, And What’s Been The Turning Point In Your Journey Since 2016?
Our goal from day one was to transform the outsourcing model. Rather than relying on traditional labor arbitrage, we focused on placing technology at the heart of every process. Stellar Innovations Bangalore launched with just 16 team members and no external investors—purely driven by purpose and vision. Nearly a decade later, we’ve scaled to 1,600 employees globally, transitioning from general outsourcing to tech-first solutions in sectors such as mortgage servicing and cybersecurity. Our expansion into the Philippines is not just about growth—it’s proof that our model is replicable on a global scale.
With A Growing Global Footprint, How Do You Keep Teams Connected And Aligned?
Our formula is built on two pillars: trust and ownership. Whether it's our offices in Dallas or Dubai, we function like tightly bonded teams. What makes Stellar Innovations unique is our leadership pipeline—90% of our executives began their careers here as interns. Our 97% retention rate speaks volumes. When a junior analyst in Bangalore has the authority to innovate processes that impact U.S. mortgage operations, you’re no longer managing employees—you’re empowering leaders.
What Differentiates Your Approach In Complex Domains Like Tax Servicing And Cybersecurity?
We don’t view industries as verticals—we treat them like tech challenges waiting to be solved. During the 30% mortgage market decline in the U.S., most firms scaled back. Stellar Innovations, however, doubled client acquisitions and grew revenue by 54%. We did it by applying cutting-edge tech like AI-based risk models and blockchain-backed audit systems. Our philosophy is simple: if something’s always been done a certain way, it’s probably due for disruption.
With Ai And Cybersecurity Evolving Fast, How Does Stellar Stay Ahead?
While many talk about emerging tech, we focus on practical implementation. Our team at Stellar Innovations Bangalore recently partnered with mortgage experts to deploy generative AI, resulting in a 40% drop in underwriting errors. In cybersecurity, our approach goes beyond patching vulnerabilities—we simulate real-world attacks monthly using ethical hackers to test our systems. Innovation here isn’t theoretical; it’s operational.
What’s Next On The Horizon For Stellar Innovations?
We’re stepping into telecom and genomics—two high-potential sectors. Our planned acquisition of a telecom company in Germany will help us apply predictive AI to 5G network management. At the same time, our genomics venture, Mediomix, is pioneering quantum computing solutions to cut DNA sequencing times from weeks to mere hours. In five years, Stellar Innovations aims to become the invisible infrastructure behind industries that people rely on daily—without even realizing it.
Conclusion
From its origin as a small startup in Bangalore to a global leader in tech-led outsourcing, Stellar Innovations Pvt Ltd continues to break new ground under the leadership of CEO Anish Thomas. By staying ahead of technology trends and empowering its people, Stellar Innovations is not just scaling—it’s reshaping the future of multiple industries.
#Stellar Innovations CEO#Anish Thomas#Stellar Innovations CEO Anish Thomas#stellar innovations#stellar innovations bangalore#stellar innovations pvt ltd ceo
0 notes
Text
Unlocking the Power of MikroTik Router for Advanced Networking
In today’s connected world, a reliable and flexible network is vital for both homes and businesses. One of the most popular choices for advanced yet affordable network management is the MikroTik Router. Known for its powerful performance, versatility, and cost-effectiveness, MikroTik has become a go-to brand for network professionals, system integrators, and tech-savvy home users alike.

Why Choose MikroTik?
MikroTik offers a wide range of products including Cloud Router Switch, POE devices, and RouterBOARD units. Each device runs on RouterOS, MikroTik's proprietary operating system that enables robust network customization. From simple routing tasks to complex traffic shaping and VLAN Setup, RouterOS delivers enterprise-level features at a fraction of the cost.
Whether you're managing a small office or setting up a router for home, MikroTik routers are engineered to scale with your needs. Their wide range of routers and switches ensures seamless integration across various network topologies.
Features That Set MikroTik Apart
1. Advanced VLAN Setup
VLANs (Virtual Local Area Networks) are critical for network segmentation, especially in business environments. MikroTik makes VLAN setup straightforward through RouterOS, allowing administrators to isolate traffic and enhance network security with minimal configuration.
2. Powerful Firewall Rules
Security is a top concern in any network. MikroTik routers include comprehensive firewall rules that help control inbound and outbound traffic. You can create custom rules to block unwanted connections, prevent DDoS attacks, and safeguard sensitive data.
3. Effortless Port Forwarding
Need to access a server or camera remotely? Port forwarding on MikroTik routers is quick and efficient. With a few settings in RouterOS, you can open specific ports and control traffic direction without compromising network security.
4. Reliable Firmware Update
Frequent firmware updates keep your MikroTik devices secure and efficient. Updates often include performance enhancements, bug fixes, and new features that extend the functionality of your router or switch.
5. Versatile POE Support
For those using IP cameras or VoIP phones, MikroTik’s POE support (Power over Ethernet) simplifies device setup by combining power and data over a single cable. This reduces clutter and minimizes the need for additional power adapters.
Comparing MikroTik vs Ubiquiti
A common debate in networking circles is MikroTik vs Ubiquiti. While both brands offer robust networking solutions, MikroTik excels in customization and cost-effectiveness. Ubiquiti may offer a more user-friendly interface, but MikroTik stands out for users who want deeper control and scriptable configurations.
For advanced users or network engineers, MikroTik is often preferred due to the flexibility of RouterOS and the sheer variety of available tools. Whether it’s traffic control, bandwidth management, or setting up firewall rules, MikroTik provides granular control unmatched by most competitors.
Ideal Use Cases
MikroTik routers and switches are used across various industries including telecom, education, hospitality, and enterprise IT. Even as a router for home, MikroTik delivers far more functionality than traditional consumer-grade equipment. With advanced features like VLAN setup, port forwarding, and firewall rules, users can enjoy enterprise-grade performance at home.
If you're deploying a network with multiple access points, the Cloud Router Switch series provides excellent backbone support. Combine that with RouterBOARD for specialized applications and you have a complete network solution tailored to your needs.
Conclusion
Whether you're building a network from the ground up or upgrading your existing infrastructure, a MikroTik Router offers unmatched value and capability. With features like RouterOS, POE, firmwareupdates, and flexible switches, MikroTik is ideal for both beginners and professionals. From router for home to enterprise networking, MikroTik delivers reliable, scalable, and secure solutions.
0 notes
Text
What documents are required for ISO 27001 Certification in Saudi Arabia?

What is ISO 27001 Certification?
ISO 27001 certification in Saudi Arabia is a worldwide standard created by the Worldwide Organization for Standardization (ISO). It characterizes the rules for the base, utilization back, and steady change of the quality of a data security administration structure (ISMS ).
This certification helps businesses:
Secure mystery information
Be mindful of the dangers ISO 27001 consultant in Saudi Arabia related to data.
Secure against cyberattacks as well as unauthorized access.
Maintain the watchfulness of data and guarantee availability.
Why is ISO 27001 Certification Basic in Saudi Arabia?
ISO 27001 consultant in Saudi Arabia is encountering fast mechanical progression as portion of Vision 2030 that consolidates making strides shrewd cities Fintech progressed government, cloud computing. A developing cybersecurity danger has led to the need for standard security frameworks.
ISO 27001 Certification in Saudi Arabia underpins organizations through:
It is partnered with the NCA (National Cybersecurity Specialist) security controls for Compliance.
Security benchmarks for information security and IT administration have been in place.
reduces the hazard of being exposed to cyber-attacks and security breaches
Enhancing competitiveness both in the open and private sectors
Enhancing responsibility towards clients, accomplices, and regulators
Who Needs ISO 27001 Certification in Saudi Arabia?
ISO 27001 consultant services in Saudi Arabia applies to any organization managing sensitive or personal information. This includes:
It programs as well as benefits providers
Banks and monetary education.
Health and Security companies
Projects for Keen City
cloud and telecom benefit providers
Educational and inquiring ISO 27001 consultant services in Saudi Arabia about institutions
Benefits of ISO 27001 Certification in Saudi Arabia
Legal Compliance guarantees Compliance with the NCA and SAMA cybersecurity guidelines.
Reducing Hazard Appraisal recognizes and supervises the security of data.
Reputation Administration works with accomplices, clients, and all other participants.
Business coherence can offer assistance to make it beyond any doubt that data is open and recoverable.
Benefits from advertising competition: Takes progress in the capability of government contracts and tenders.
“Customers’ Believe” illustrates the commitment to securing delicate information.
Key Steps to Fulfill ISO 27001 Certification
Gap Examination Survey: current security measures to defend your data.
Risk Assessment: Recognize blemishes and plan techniques to address them.
ISMS records : Create methodologies, strategies, and security ISO 27001 auditor in Saudi Arabia controls
Application: Overhaul ISMS upgrades offices and frameworks
Internal Review: Survey and affirm ISMS effectiveness
Review Administration Audit: Ensure consideration of specialists ISO 27001 auditor in Saudi Arabia in the decision-making process
Security Reviews Make it beyond any doubt that you are following the standard audit to the letter without any doubt.
Required Documents for ISO 27001 Certification
Information Security Policy
Risk Examination and Chance Treatment Plan
Statement of Suitability (SoA)
Access Control Policy
Incident Organization Procedure
Asset Stock and Classification
Internal Survey and Organization Overview Reports
How Long Does It Take?
ISO 27001 execution can take anywhere from 3 to 6 months, based on:
The estimation of an organization, as well as the level of complexity
Several places
The display IT systems aren’t as well-established.
Internal assets are accessible.
Cost of ISO 27001 Certification in Saudi Arabia
The Gotten is based on:
The estimate of the operation and trade
Scope of the ISMS
Controls for industry and levels of hazard
The Certification body is chosen.
Factocert offers custom and reasonable ISO 27001 bundles for companies in Saudi Arabia.
Why Factocert for ISO 27001 Certification in Saudi Arabia?
We provide the best ISO Consultants in Saudi Arabia who are knowledgeable and provide the best solutions. Kindly contact us at [email protected]. ISO Certification consultants in Saudi Arabia and ISO auditors in Saudi Arabia work according to ISO standards and help organizations implement ISO consultant services in Saudi Arabia Certification with proper documentation.
For more information, visit ISO 27001 certification in Saudi Arabia
0 notes
Quote
セキュリティ会社プルーフポイントの研究者らは月曜日、数十の組織から機密データや金融資産を盗むことを目的とした進行中のキャンペーンにおいて、一部は上級幹部のものを含む数百のMicrosoft Azureアカウントが未知の攻撃者の標的になっていると発表した。 このキャンペーンは、資格情報フィッシングとアカウント乗っ取りの手法を統合した電子メールをアカウント所有者に送信することにより、対象の Azure 環境を侵害しようとします。 攻撃者は、個別のフィッシング詐欺と共有ドキュメントを組み合わせて攻撃を行っています。 一部のドキュメントには、クリックするとユーザーをフィッシング Web ページにリダイレクトするリンクが埋め込まれています。 標的となった役割の広範さは、影響を受ける組織全体にわたるさまざまなリソースと責任にアクセスできるアカウントを侵害するという脅威アクターの戦略を示しています。 「脅威アクターは、さまざまな組織にわたってさまざまな肩書きを持つ幅広い個人に焦点を当てているようで、世界中の何百人ものユーザーに影響を与えている」とプルーフポイントの勧告は述べて いる 。 「影響を受けるユーザー ベースは幅広い役職に及び、セールス ディレクター、アカウント マネージャー、財務マネージャーなどが頻繁にターゲットとなります。 「運営担当副社長」、「最高財務責任者兼財務責任者」、「社長兼最高経営責任者(CEO)」などの幹部職に就いている個人も標的に含まれていた。」 アカウントが侵害されると、脅威アクターはアカウントをさまざまな形式の多要素認証に登録することで保護します。 これにより、被害者がパスワードを変更したり、ダッシュボードにアクセスして最近のログインを調べたりすることが困難になる可能性があります。 場合によっては、使用される MFA は、テキスト メッセージまたは電話で送信されるワンタイム パスワードに依存します。 ただし、ほとんどの場合、攻撃者は通知とコードを備えた認証アプリを使用します。 拡大 / 侵害されたクラウド テナント内の攻撃者によって実行された MFA 操作イベントの例。 プルーフポイント Proofpoint は、次のような他の侵害後のアクションを観察しました。 データの引き出し。 攻撃者は、金融資産、内部セキュリティ プロトコル、ユーザー資格情報などの機密ファイルにアクセスしてダウンロードします。 内部および外部のフィッシング。 メール���ックス アクセスは、影響を受ける組織内で横方向の移動を実施し、特定のユーザー アカウントをパーソナライズされたフィッシング脅威でターゲットにするために利用されます。 Financial fraud. In an effort to perpetrate financial fraud, internal email messages are dispatched to target Human Resources and Financial departments within affected organizations. Mailbox rules. Attackers create dedicated obfuscation rules intended to cover their tracks and erase all evidence of malicious activity from victims’ mailboxes. Advertisement Enlarge / Examples of obfuscation mailbox rules created by attackers following successful account takeover. Proofpoint The compromises are coming from several proxies that act as intermediaries between the attackers’ originating infrastructure and the accounts being targeted. The proxies help the attackers align the geographical location assigned to the connecting IP address with the region of the target. This helps to bypass various geofencing policies that restrict the number and location of IP addresses that can access the targeted system. The proxy services often change mid-campaign, a strategy that makes it harder for those defending against the attacks to block the IPs where the malicious activities originate. Other techniques designed to obfuscate the attackers' operational infrastructure include data hosting services and compromised domains. “Beyond the use of proxy services, we have seen attackers utilize certain local fixed-line ISPs, potentially exposing their geographical locations,” Monday’s post stated. “Notable among these non-proxy sources are the Russia-based 'Selena Telecom LLC', and Nigerian providers 'Airtel Networks Limited' and 'MTN Nigeria Communication Limited.' While Proofpoint has not currently attributed this campaign to any known threat actor, there is a possibility that Russian and Nigerian attackers may be involved, drawing parallels to previous cloud attacks.” How to check if you’re a target There are several telltale signs of targeting. The most helpful one is a specific user agent used during the access phase of the attack: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Attackers predominantly utilize this user-agent to access the 'OfficeHome' sign-in application along with unauthorized access to additional native Microsoft365 apps, such as: Office365 Shell WCSS-Client (indicative of browser access to Office365 applications) Office 365 Exchange Online (indicative of post-compromise mailbox abuse, data exfiltration, and email threats proliferation) My Signins (used by attackers for MFA manipulation) My Apps My Profile Proofpoint included the following Indicators of compromise: Indicator Type Description Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access phase Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access and post-access phases Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access and post-access phases sachacel[.]ru Domain Domain used for targeted phishing threats lobnya[.]com Domain Source domain used as malicious infrastructure makeapp[.]today Domain Source domain used as malicious infrastructure alexhost[.]com Domain Source domain used as malicious infrastructure mol[.]ru Domain Source domain used as malicious infrastructure smartape[.]net Domain Source domain used as malicious infrastructure airtel[.]com Domain Source domain used as malicious infrastructure mtnonline[.]com Domain Source domain used as malicious infrastructure acedatacenter[.]com Domain Source domain used as malicious infrastructure Sokolov Dmitry Nikolaevich ISP Source ISP used as malicious infrastructure Dom Tehniki Ltd ISP Source ISP used as malicious infrastructure Selena Telecom LLC ISP Source ISP used as malicious infrastructure As the campaign is ongoing, Proofpoint may update the indicators as more become available. The company advised companies to pay close attention to the user agent and source domains of incoming connections to employee accounts. Other helpful defenses are employing security defenses that look for signs of both initial account compromise and post-compromise activities, identifying initial vectors of compromise such as phishing, malware, or impersonation, and putting in place auto-remediation policies to drive out attackers quickly in the event they get in.
進行中のキャンペーンにより上級幹部の Azure アカウントが侵害され、MFA を使用してアカウントがロックされる | アルス テクニカ
0 notes
Text
{🫡 Dave} The Senate has promoted Air Force officer Timothy Haugh from lieutenant general to general and confirmed him as the new director of the NSA and head of Cyber Command. He will replace Paul Nakasone, who has served since May 2018.

↪️ In some ways this looks like a destructive attack similar to the VIASAT hack at the start of the war. But it differs in far more significant ways.
In similarities, the hack has some military implications: firstly a lot of air raid warning systems are now offline, and secondly a lot of Ukrainian military communications is done over mobile phone.
The attack won’t be as damaging to military communications as the VIASAT hack. Ukraine’s mobile telecommunications systems have been configured for increased resilience to disruption.
The three carriers all accept customers from other networks so if there is any signal from any network at all, people can make phone calls and get internet.
That said, Kyivstar is the top carrier in Ukraine. It has 26m subscribers, almost as much as the other two carriers (Vodafone 19m, and Lifecell 9m) combined.
Disrupting Kyivstar means 50% of mobile subscribers lose their main carrier. Half of the country’s mobile telephony infrastructure is offline. This will cause congestion and overloading on the remaining carriers’ networks.
This sort of attack shapes the battle space and creates conditions that can be exploited. For example, I would think that the front lines and the ISR (intelligence, surveillance, reconnaissance) drone operators will have less bandwidth to communicate with artillery and other support elements. This will decrease their operational capacity and reduce their defensive capabilities.
It isn’t clear yet whether this attack was coordinated with any other actions. I would expect some attempt to exploit this, otherwise it is just adding friction to daily life for a short time. Unpleasant, but not strategically significant.
Maybe they are literally just trying to make people’s lives miserable?
It is worth keeping an eye out to see if there are further attacks on telcos. Taking down all of the telecom providers would be an effective attack. Sure, mobile internet isn’t the critical component of military communications… but it is damn hard to run a modern war without a data link.

youtube


1 note
·
View note
Text
Isn't the CCP Warmonger? Timeline after 2019 Hong Kong Protests
While the world takes 2019 Hong Kong Protests as Hongkong people's voice against the CCP's unilateral breach of the Sino-British Joint Declaration on Hong Kong, the CCP insists that it was a subversion attempt of the CCP regime by external forces. Every one who knows the CCP understands that suppressing the Protests wouldn't be the ending. I think the following tweet may reflect the CCP's ideology:

"https://twitter.com/davinton_com/status/1732564815141638197"
Why do I think this person is voicing the CCP's ideology? In the post he pinned, he said "my only position is to put the national interests as the 1st priority" and the country he was referring to was obviously China.

"https://twitter.com/davinton_com/status/1721104412540891588"
Bearing in mind, there has always been different factions of the CCP fighting each other for the top power. It's also well acknowledged that certain factions of the CCP somehow weaponized Hong Kong Protests in order to take over Beijing but failed.
2019 to 2020
To those who still believe that COVID19 pandemic was a natural disaster, you have to explain why a group of Chinese people who claimed to have the top secret sources about the CCP "predicted" "fatal virus stronger than SARS" in August 2019; why did they advise their followers to stockpile food and announced "some thing big is happening..." on November 30, 2019 or even earlier? We later learned that the 1st COVID19 case in records was found on December 1, 2019. It was also them who firstly introduced Hydroxychloroquine as the treatment for coronavirus disease (COVID19), the unprecedented disease in the human history. Why did Beijing close down Wuhan city but remain the international air flights open to the world?
All of those may be "co-incident" but the PLA does have its bioweapon plans announced years ago and their book "Unrestricted Warfare" was published with the subtitle "China's Master Plan to Destroy America".

"https://archive.org/details/isbn_9780971680722"
Myanmar Coup in 2021
The Myanmar Coup took place on the morning of Feb. 1st, 2021, deposed the democratically elected members of NLD and Myanmar's military took the power.
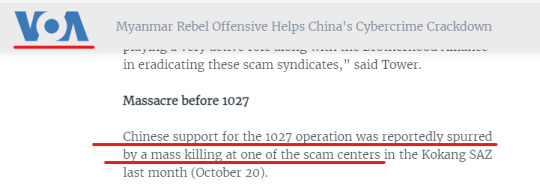
The CCP's tie with Myanmar's military has only recently surfaced to the public following the media's report about China's Cybercrime Crackdown in Myanmar and the Operation 1027.
"https://www.voanews.com/a/myanmar-rebel-offensive-helps-china-s-cybercrime-crackdown/7362836.html"
As per VOA's report, "Myanmar rebels have launched a series of coordinated attacks known as “Operation 1027” that outside analysts say have given them new momentum in their struggle against the military junta. The operation also reportedly aligns with China’s interest in cracking down on transnational crime in the region, particularly cybercriminals who target Chinese consumers."
"https://www.voanews.com/a/myanmar-rebel-offensive-helps-china-s-cybercrime-crackdown/7362836.html"
Behind the VOA's narrative that is probably approved by Beijing, here is what we heard from other channels.
The so-called "Myanmar rebels" had no money, hundreds people, and no weapons, before "Operation 1027", within few days, they managed to form troops with thousands of soldiers, obtained sophisticated weapons and accurate intelligence cooperation.

"https://www.youtube.com/watch?v=vkCNgyRDA-8"
Why? According to @tankman2002 who used to be a criminal investigator/police in China, on Oct. 20, there was a mass killing of Chinese people who were trying to escape from Crouching Tiger Villa/卧虎山庄, a telecom scam compound in Kokang, Myanmar. Four under-covered Chinese intelligence officers who organized the runaway were buried alive after they showed up their official identity. People may have the same question as I had, why did these officers reveal their identity after the runaway plan failed? It goes back to the CCP's support and cultivation of Myanmar Communist Party and Military warlords, the CCP is like the big brother of the Myanmar military warlords. The latter were supposed to show respect to Beijing, not dared to kill Beijing's official representatives.
VOA's report corresponds to the above mentioned details but not to the history between the CCP and the Myanmar military warlords.

Whereas @tankman2002 pointed that the CCP's strategy was "killing with borrowed knife/借刀杀人": "attack using the strength of another when in a situation where using one's own strength is not favorable. For example, trick an ally into attacking them or use the enemy's own strength against them. The idea is to cause damage to the enemy via a third party."
"https://en.wikipedia.org/wiki/Thirty-Six_Stratagems"
The borrowed knife, referred to as "Myanmar rebels" by VOA, is the Myanmar National Democratic Alliance Army, MNDAA. Before Operation 1027, MNDAA was the weakest force among the armed organizations in Kokang, no money, no weapon and no soldiers. On Oct. 27, after Beijing government was determined to retaliate, the leader of MNDAA suddenly issued an open letter to Myanmar people, declared a war against the telecom fraud, with weapons, soldiers and accurate intelligence co-operation ready. By the way, it reflects the CCP's double standards, while criticizing Israel's counter-fight against Hamas' terrorist attacks, the CCP took a flash retaliatory military action and cleaned up the military and telecom scam group in Myanmar.
Another media report likely from China on the Operation 1027 is similar to @tankman2002's report, except it covered-up the source of the weapons that MNDAA obtained as "mysterious" and "unknown".
"https://twitter.com/maoshen04/status/1724477083680649245"
According to @tankman2002, Kokang, where many telecom scam centers located used to be part of China in the history, the language and culture there are same as that of Yunnan, China. Kokang even shares with China the telecommunications networks, area code and the currency: RMB.

"https://www.youtube.com/watch?v=vkCNgyRDA-8
In his YouTube video, @tankman2002 presented details about China's export of the Communism to southeast Asian countries in 1960s and said the CCP's attempt to overturn those countries' government was the reason of the anti-Chinese sentiment and violence at that time. China trained Myanmar Communist leaders in Beijing, sent Myanmar Communist key personnel to the 54th Field Army of the PLA to study. Pheung Kya-shin, the chairman of the Kokang Special Region in Myanmar (Burma) and the leader of the Myanmar National Democratic Alliance Army (MNDAA), was one of them.


In July 1967, China's official media openly appealed that "Firmly support the armed struggle of the Myanmar people under the leadership of the Communist Party of Myanmar". They dispatched military advisory team to Myanmar, sent PLA soldiers to join Myanmar Communist's military force.
By the way, @tankman2002 is not the only one who revealed the close tie between the CCP and the Myanmar Military forces as you can see below:
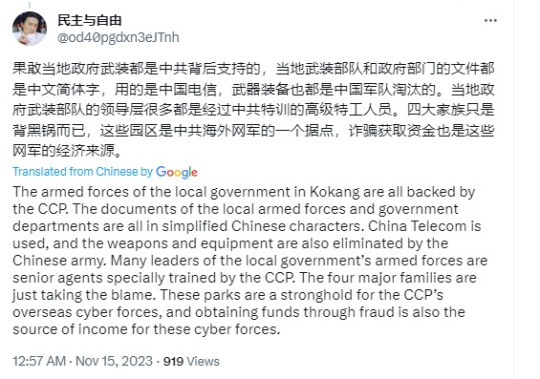
Someone even pointed finger at the CCP for the telecom scam:

Echo to the above allegation, the CCP officially revealed that two wanted fugitives in the telecom fraud case of Myanmar Bai Yinglan/白应兰, aka Li Mengna/李梦娜 and Wei Rong/魏榕, aka Chen Rong/陈榕,actually have their civil registration record in China! They are literally Chinese! For those who don't understand China's Civil Registration System/户籍制度,it's a system that records every natural citizen born in China.

"https://www.wenxuecity.com/news/2023/12/11/125316836.html"

"https://www.wenxuecity.com/news/2023/12/11/125316836.html"
As for the CCP's proxy war strategy in 1027 Operation, here are Mark Yang's words in his article: "(China) executed a comprehensive operation through proxies to completely solve the problem of telecom fraud in northern Myanmar".
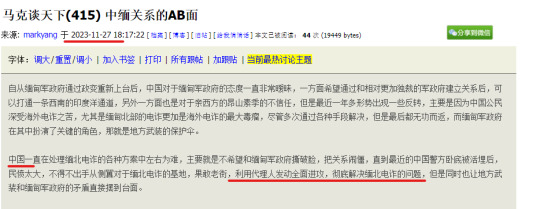
"https://bbs.wenxuecity.com/bbs/mychina/1086458.html"
Note that on the official website of the Chinese Ministry of Foreign Affairs, we can find the following statement "we have never invaded other countries, nor engaged in proxy wars..." Turns out, they are saying one thing and doing another.
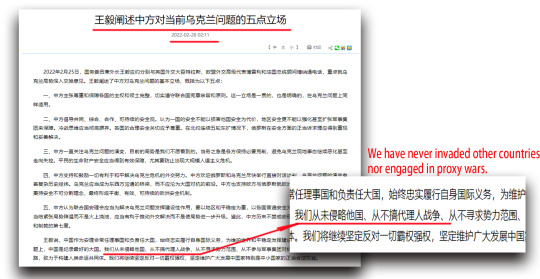
"https://www.mfa.gov.cn/web/wjbzhd/202202/t20220226_10645790.shtml"
Russia's Invasion of Ukraine in 2022
There is a Wikipedia page created for "China and the Russian invasion of Ukraine" saying "following the Russian invasion of Ukraine, China's position has been ambivalent. On one hand, it has blamed enlargement of NATO, which Russia has stated as a reason for starting the war. On the other hand, it has stressed respect for Ukraine's territorial integrity."
I think the page was created by western people because the CCP's position isn't "ambivalent" at all, in my point of view. The CCP's pro-Russia position is for real whereas its so-called "respect for Ukraine's territorial integrity" is merely a diplomatic cliché saved as a justification for its military invasion of Taiwan under the One China policy.

"https://en.wikipedia.org/wiki/China_and_the_Russian_invasion_of_Ukraine#:~:text=Following%20the%20Russian%20invasion%20of,respect%20for%20Ukraine's%20territorial%20integrity."
The CCP's fake respect for Ukraine's territorial integrity can be proven by removing the official statement published on Jan. 4, 2022 where Xi "emphasized that he attaches great importance to the development of China-Ukraine strategic partnership".
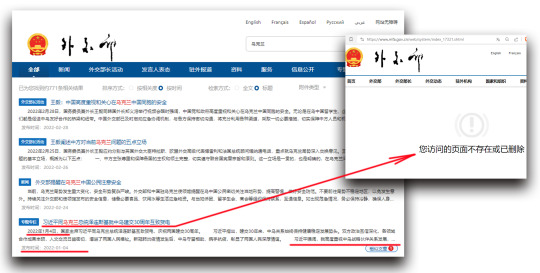
"https://www.mfa.gov.cn/web/system/index_17321.shtml"
On April 18, 2023, An article was published on the CCP's mouthpiece web side 红歌会: "China's Defense Minister's visit to Russia Has Made the US and NATO to tremble".
In the article, it says "China needs a strong and successful Russia. Here is the message to the US: except military aid to Russia to attack Ukraine, China is doing everything else". Meanwhile, it sets the bottom line: "anyone who wants to dismember and destroy Russia, you step on China's bottom line" and repeated again the China-Russia joint-declaration "China needs a strong and successful Russia".
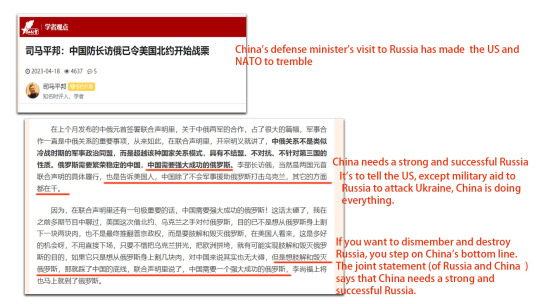
"https://m.szhgh.com/Article/opinion/xuezhe/2023-04-18/325059.html"
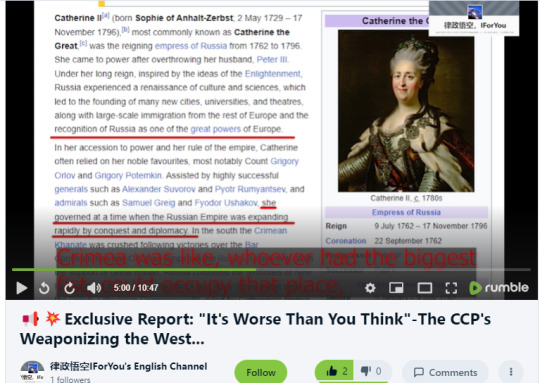
As for the CCP's intention of using Russia's invasion of Ukraine as a proxy war and a test for its military attack against Taiwan, copying Russia's recovery of Crimea, here is what I heard in Twitter Space:
Please click the link below to my Rumble video and listen from 4:50
"https://rumble.com/v2h4hyk-exclusive-report-its-worse-than-you-think-the-ccps-weaponizing-the-west….html"
More over, the CCP used Elon Musk, the new power stepped into the global politics, to lead the public opinion towards in favor of China-Russia Alliance. On Feb. 23, 2023, Elon Musk posted "A Russia-China alliance is inevitable. It will grow much stronger over time".
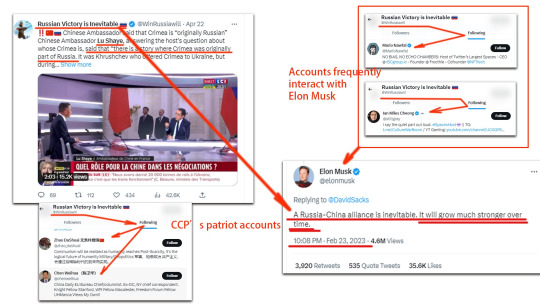
CCP, Russia and Elon Musk: World Totalitarian Alliance in Construction?
Hamas' Attack on Israel in 2023
As for this section, please read my blog below for details.
Who’s Behind the Hamas Attack?
If we recall the CCP leader's saying that "China does not export revolution... and it does not mess around with you", it was not true in the CCP's history, and it still remains in question when we review Myanmar Coup in 2021, Russia's invasion of Ukraine in 2022 and Hamas' attacks on Israel in 2023.
(To be updated)
0 notes
Text
Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has launched some of the most disruptive cyberattacks in history against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv.
On Tuesday, a cyberattack hit Kyivstar, one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a statement posted by Ukraine’s Computer Emergency Response Team, or CERT-UA.
Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, according to Reuters, that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.”
“We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.”
The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU.
“We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!”
Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.”
If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a wide variety of covers, hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its attack on the 2018 Winter Olympics.
Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information.
While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched more data-destroying wiper attacks on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled thousands of Viasat satellite modems across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, caused a blackout in a Ukrainian city just as it was being hit by missile strikes, potentially hampering defensive efforts.
It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids.
“Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
44 notes
·
View notes
Text
An “ultra-left militant” was arrested in north-west France on Sunday after being found behaving suspiciously near a railway site, according to police sources quoted by French media.
Officers who searched the man’s car found keys to technical premises, pliers, a set of universal keys and literature “linked to the ultra-left".
The 28-year-old suspect is currently being questioned by police in the city of Rouen, French media said.
There is no indication that the man has links with the people responsible for Friday's suspected co-ordinated arson attack on railway lines ahead of the opening ceremony for the Paris Olympic Games.
The acts of sabotage paralysed high-speed TGV lines running to and from Paris and heavily disrupted travel in France.
On Monday morning, France’s Minister of the Interior Gerald Darmanin said that a “number of profiles of people who could have committed these very deliberate, very targeted acts of sabotage” had been identified.
He added that the methods employed were “traditional” of the ultra-left and said there was “likely a political claim” behind the sabotage.
"The question is whether they were manipulated or is it for their own account," Mr Darmanin said, adding that investigators were making good progress and would find those responsible.
Although he stopped short of saying the saboteurs had accomplices within France's national rail operator SNCF, Mr Darmanin noted the locations of the arson attacks were “extremely specific”
“It was obviously extremely well targeted, it wasn't done randomly, and it affected three major lines," he added.
Mr Darmanin also said that around 50 people were arrested ahead of the Olympics who, alongside others - thought to number around 150 - had “wanted to carry out either sabotage or radical protests in Paris during the first events of the Olympic Games”.
Alongside the damage to the train lines, French media also reported that fiber optic cables were found cut in six locations across France overnight Sunday into Monday, causing some isolated outages.
It is still unclear at this stage whether there are any links between the vandalism on the telecoms installations and the sabotage on the rail network last week, which affected an estimated 250,000 passengers on Friday and hundreds of thousands more over the weekend.
No group has yet claimed responsibility for either incident. One security source suggested in French media last week that the arson attacks bore all the hallmarks of the extreme left.
Transport minister Patrice Vergriete said on Monday that trains services were back up and running as normal after teams worked around the clock over the weekend to fix the damage.
He added that "considerable means”, including drones and police helicopters, were deployed to strengthen the security of the thousands of kilometres that make up France’s railway network.
Mr Vergriete also said that the acts of sabotage will likely have cost several million euros.
3 notes
·
View notes